Without Network Monitoring, there is no good way to get a real-time view of your connected environment. But with Network Monitoring reports, you can look backwards to spot problems and trends. Just as vital are logs that deepen this rear-view mirror look, as they contain all the data for all the elements you are monitoring.
To support security forensics and truly understand the network, Smart IT pros implement network log management best practices (which start with logging and analyzing in the first place).
So, What Exactly Are Network Monitoring Logs?
A Network Monitoring log is a "journal-of-record" for every event or transaction that takes place on a server, computer or piece of hardware on your network. Just about everything in your IT environment has some kind of log. Microsoft systems generate Windows Event Log files. UNIX-based servers and devices use the System Log (or Syslog) standard. Apache and IIS generate W3C/IIS log files.
Log files contain a wealth of information to reduce an organization’s exposure to intruders, malware, damage, loss and legal liabilities. Log data needs to be collected, stored, analyzed and monitored to meet and report on regulatory compliance standards like Sarbanes Oxley, Basel II, HIPAA, GLB, FISMA, PCI DSS and NISPOM. This is a daunting task since log files come from many different sources, in different formats and in massive volumes, and many organizations don’t have a proper log management strategy in place to monitor and secure their network.
So Why Do Network Monitoring Log Management?
In the case of your network, the log contains a detailed record of everything that happened—including user actions. And by network, that includes any network resource you choose to monitor, including servers, devices, applications such as databases and websites, etc. The record includes events and performance data, which is great for applications but also critical for knowing how network pieces have performed over time.
Logs are everywhere. “Everything in your enterprise’s IT environment—your servers, firewalls, IT equipment, etc.—generate logs about their activities and the events they encounter. They store these logs, which can total in the terabytes, on local and remote servers. Trying to find all these logs by hand goes beyond the exhausting and the painful—it might be actively impossible to handle the overwhelming amount of IT information. That’s where a log management solution comes in,” explained Solutions Review.
Network Log Management Options
IT pros have several options when it comes to log management, and many cost more than they need to and are not designed for network logs. There are dedicated log management solutions as well as SIEM, which many use for log management—but it’s overkill unless you need the full feature set of Security Information and Event Management (SIEM) tools and don’t mind the cost and complexity.
Dedicated log management and SIEM solutions are not always the best when it comes to doing something with all that network data. First, they can be difficult to set up to gather network events. And they are not designed to offer a deep and easy understanding of all this information.
Here is what Solutions Review had to say: “Traditional log management solutions are designed to do their simple task well but aren’t designed to do anything else. But if you want to utilize the collected logs to extract key metrics from your system, mandate your enterprise’s cybersecurity team to dive into them headfirst to extract those metrics. This makes compliance more challenging than anticipated, as finding the relevant compliance data may require serious manual correlation efforts; this constitutes another investment of time and resources. Additionally, traditional log management will have trouble with custom log formats, which can make the job of your security analytics team much harder than it already is to collect the data they need.”
Network Log Management—How WhatsUp Gold Handles Logs
Logs are critical for identifying trends and detecting patterns. This way you can go deep into identifying and understanding network activity. This information can drive future network upgrades and architectures as well as help in the design and implementation of new security measures.
WhatsUp Gold Log Management Dashboard
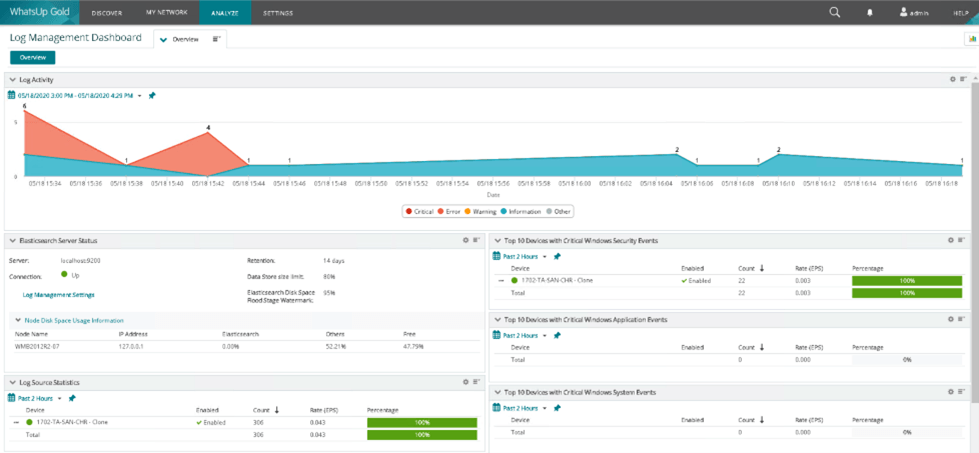
The Beauty of Integrated Log Management
The WhatsUp Gold Log Management add-on allows you to collect Windows Event Log and Syslog events from any available device configured as a log data source. In addition to simply collecting log data, you can customize WhatsUp Gold to collect events which fit your specific needs by defining search criteria and applying several common and/or format-specific filters when viewing corresponding reports and dashboard views.
WhatsUp Gold Log Management lets network and system administrators gather Windows and system logs from any device in their network and leverage WhatsUp Gold mapping, dashboarding and alerting capabilities to manage them.
WhatsUp Gold Log Management functionality provides these key advantages:
- Convenience – Manage Syslog and Windows log events and alerts via the customizable WhatsUp Gold interface.
- Focus – Extensive pre- and post-filtering capabilities reduce the firehose of logs down to the events you care about.
- Alerting – Get alerts via web, email, SMS or Slack when log status or events trigger conditions or thresholds you’ve set.
WhatsUp Gold Log Management Architecture
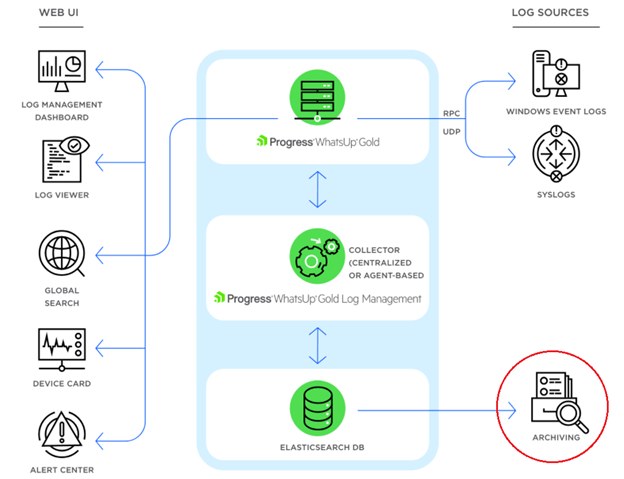
Manage syslog and Windows log events and alerts the same way you monitor the rest of the network, with the same customizable dashboards and reporting.
Get More Log Management Details
Learn everything you need to know to get started with our What is Network Log Management? eBook.
Visit our WhatsUp Gold Best Practices for Event Log Management page.
You can also try our Network Monitoring solution: Download a free fully-functional trial of WhatsUp Gold.
View All of The ABCs of Infrastructure Monitoring
Looking to start on the basics of IT infrastructure monitoring? Our alphabetized index is an excellent place to begin or extend your education. View all of our current topics.